The Art of Deception: OSINT Capture-the-Flag Walkthrough Part II
- Jemma Ward
- Aug 12, 2025
- 9 min read
This is the second part of our walkthrough for our July Capture-the-Flag The Art of Deception, in which more than 200 participants tested their OSINT skills on a series of challenges relating to the art world. You can find Part I here.
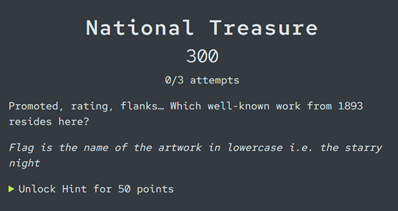
National Treasure
If you’re familiar with OSINT Capture-the-Flags, you’ve probably come across a challenge like this before (the first time I encountered one, I was stumped!). We have three words that correspond to a location – is it a riddle, or some kind of anagram? In this case, no. Instead, it’s a hint that we need to find some kind of tool or technique that uses three seemingly random words to identify a specific location. When in doubt, Google to the rescue…
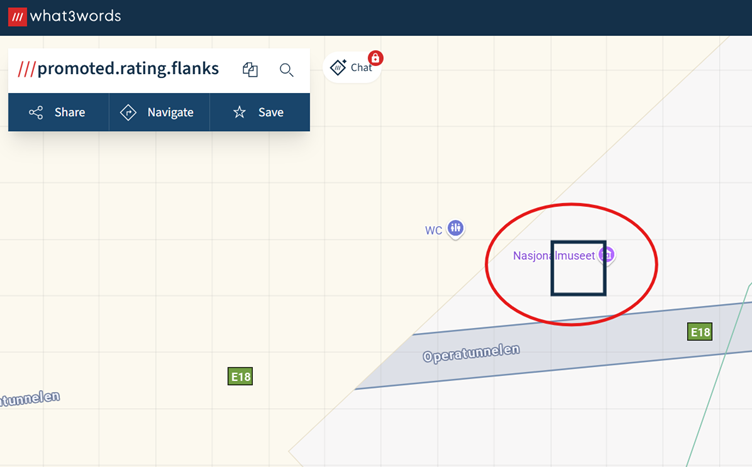
What3words is a geo-tool where every three square metres anywhere in the world is assigned a unique combination of three words. So all we need to do is enter our phrase!
It brings us to the Nasjonalmuseet, the National Museum of Norway in Oslo. A quick look at the website is probably enough to identify a very famous painting that resides there – The Scream by Edvard Munch. Verify via the artwork information (or in Wikipedia) that the correct year is 1893, and we’ve got our flag (and that’s something to scream about!).
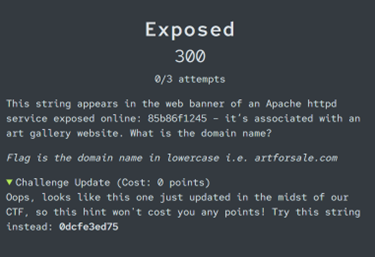
Exposed
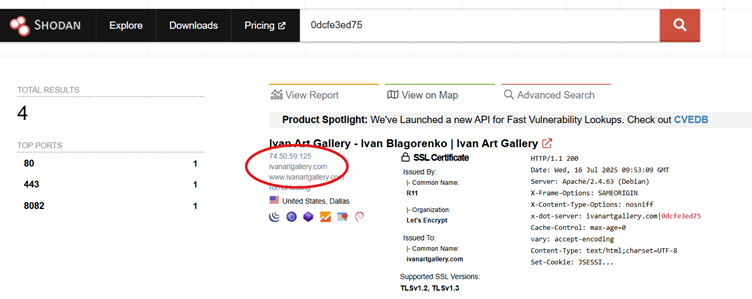
This challenge gives us an odd series of numbers and letters (looks like a hexadecimal string, don’t you think?) and we’re told it appears in the web banner of an exposed Apache httpd service. Now we need to identify which domain name (associated with an art gallery) the string is linked to.
To solve this challenge, we need to find a tool that searches for exposed services. Shodan.io is a handy search engine for internet-connected devices – it indexes metadata from exposed services and devices around the world, including things like web cams, routers, and web servers (even traffic lights!). It's a valuable OSINT tool for identifying misconfigured or publicly accessible infrastructure.
By entering the string (you might have noticed that the string updated partway through our CTF, so may look different to the screenshot below!) into Shodan’s search bar, we can pull up banners where that exact value appears. One of the results clearly associates the string with an Apache httpd service hosted by the domain ivanartgallery.com.
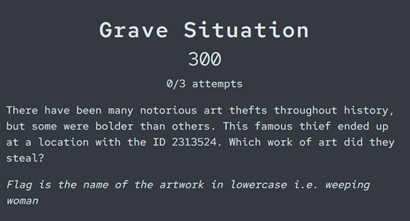
Grave Situation
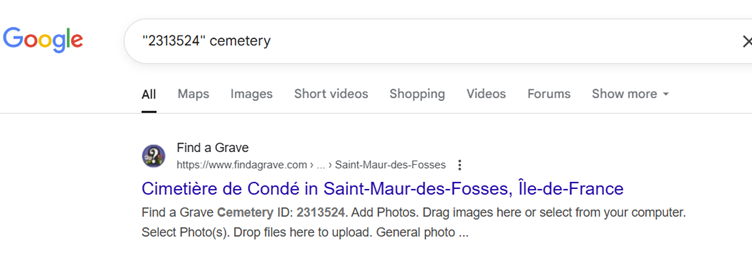
Catch that hint up in the challenge name? Even if you didn’t, you could probably still craft some search strings to find what you’re looking for. Searching for the number itself will, technically, retrieve a relevant site, but it only appears around the seventh page of Google’s result.
Matching our number with a keyword like ‘grave’ or ‘cemetery’, however, will reveal that it is the ID of Cimetière de Condé.
Ancestry and cemetery records can be useful sources of open-source information - not necessarily for current POIs, of course, but they often reveal details like family connections and common last names for areas of interest.
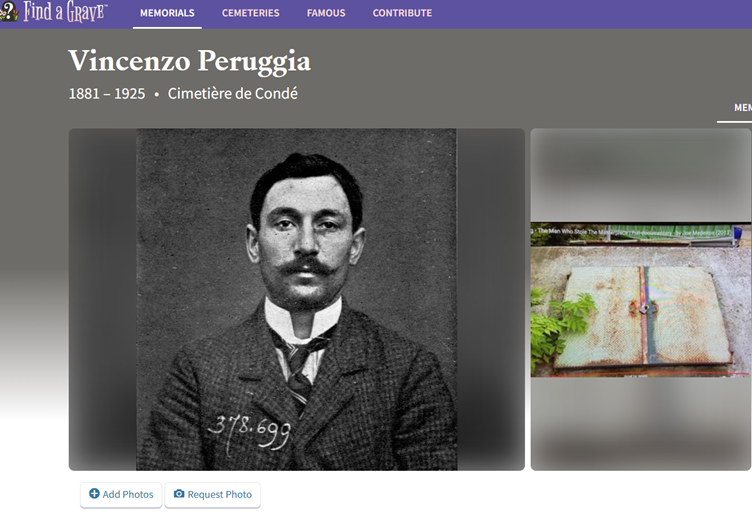
The next step is to find out whether any famous (or notorious) individuals were buried there. Taking our cemetery name and adding keywords like ‘famous burials’ will identify Vincenzo Peruggia, who perpetrated one of the most famous art heists in history – he stole the Mona Lisa from the Louvre in 1911.
Vermeer
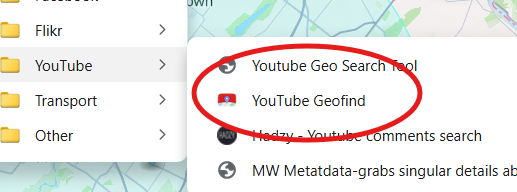
We have a location and a platform of interest – but, unfortunately, YouTube isn’t great for searching tagged locations for its videos. This is where a tool that retrieves YouTube metadata comes in handy. Within the OSINT Bookmark stack, head to the folder containing Area and Event Monitoring resources, select the Live Monitoring folder, and then YouTube tools. In there, you’ll find the useful YouTube Geofind.
YouTube Geofind allows users to search for YouTube videos tagged with locations, along with refining searches using keywords and timeframes. Not every piece of YouTube content will contain a location tag – in fact, most of them don’t. But investigating video content posted online within a specific location can be a useful way to gauge what is happening ‘on the ground’ when it comes to area and event monitoring investigations.
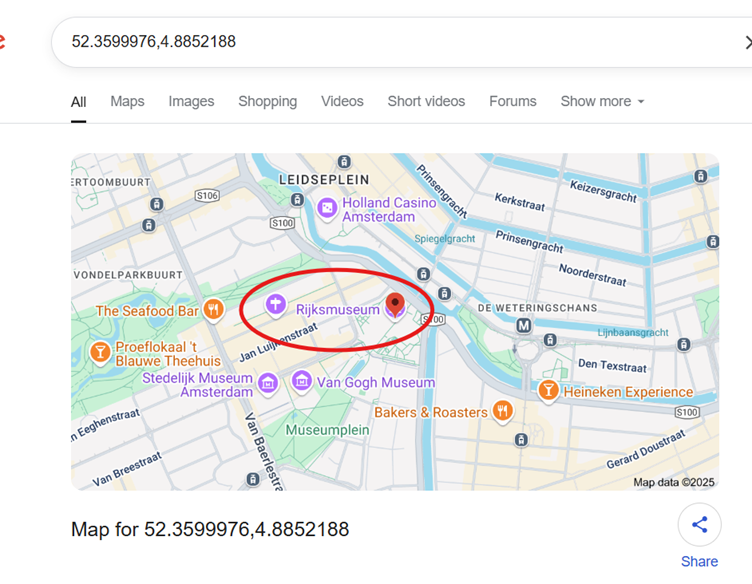
To find our flag, let’s take the key information from the challenge and craft a search. A quick Google search tells us that the coordinates are for the Rijksmuseum in Amsterdam.
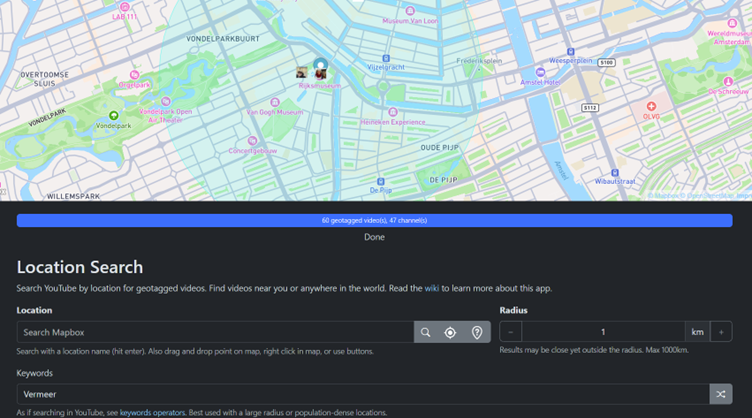
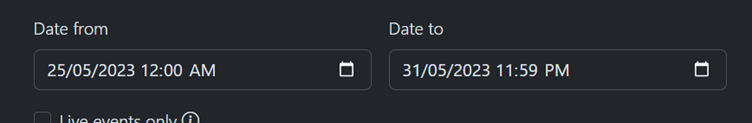
If we navigate to the Rijksmuseum within the YouTube Geofind tool, set a search radius (we’ll start small – just 1km), and add the keyword ‘Vermeer’, we end up with quite a selection of videos:
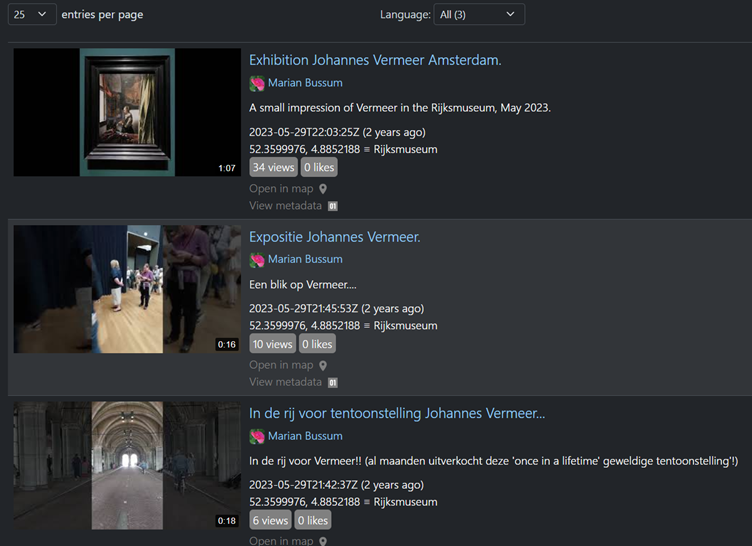
So let’s run the same search again, but include a custom date range to target the end of May 2023.
This time, we retrieve just three videos, all from the same channel, so we have our flag – the account name is Marian Bussum.
Dark Market
A dark web challenge, intriguing! For this one, we are asked to identify the username of a dark web user who posted on a well-known forum about selling a 16th century Flemish tapestry. The challenge hinted at dark web activity, meaning users would need to conduct OSINT using darknet-specific platforms.
The first step was to identify relevant dark web forums. One of the most widely used and searchable forums is Dread, a Reddit-style discussion board accessible via the Tor network. It's a popular destination for vendors, buyers, and general discussion of dark web marketplace topics.
So how do we get to Dread? Well, you’ll need the Tor browser for this one. To learn how to set up a basic virtual environment for dark web investigations, you can read our blog here: Set Up a Safe and Secure Virtual Environment for Dark Web Access.
Once you have Tor browser up and running, you’ll need to find the link to Dread. While there are a number of dark web search engines, they don’t retrieve results in the same way as surface web search engines like Google or Bing. Searching for ‘Dread’ may or may not deliver a relevant result. That’s why indexes are so useful for Dark Web research – indexes are pages sometimes hosted on the surface web, and sometimes on Tor hidden services (.onions) that provide a list of popular dark web sites.
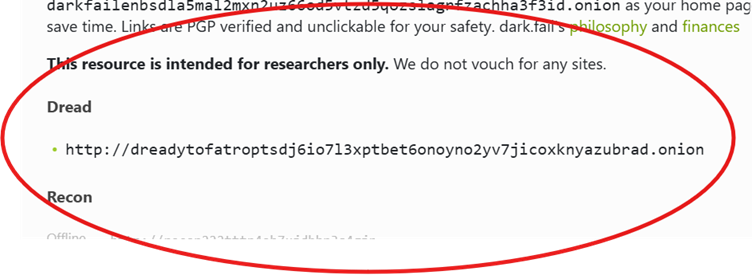
Dark.fail is one of the dark web indexes that includes a link to the Dread forums – there’s a surface web version here, although when using Tor browser you will be able to use the .onion version. It also helpfully includes an indicator of whether or not the service is currently available.
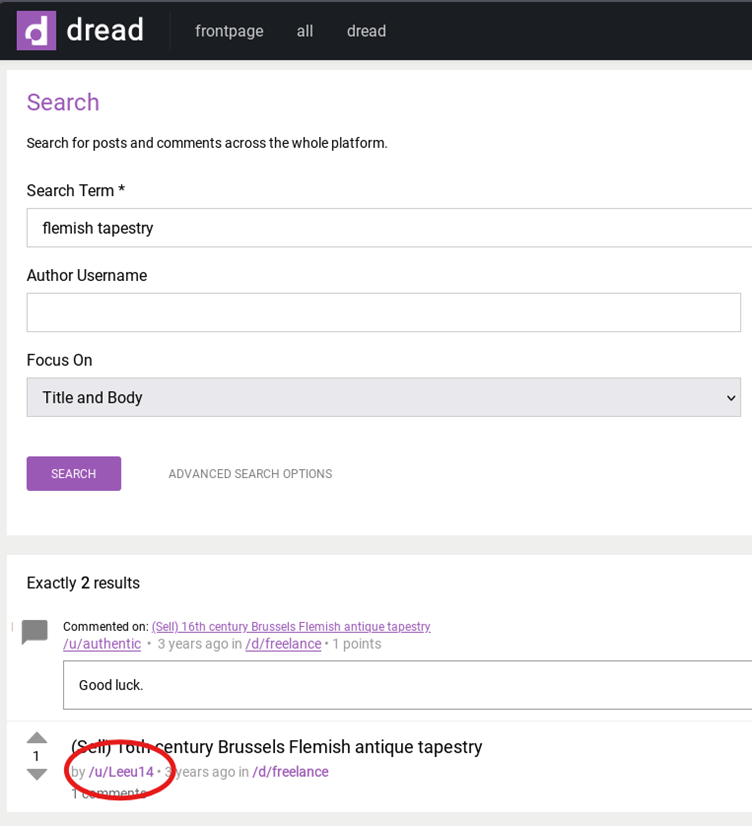
Once on Dread, we can conduct keyword searches using terms from the challenge, like ‘Flemish’ and ‘tapestry’. These searches return a small number of results, making it relatively straightforward to pinpoint the relevant posts.
The user in question posted twice about a 16th-century tapestry they were trying to sell. Their username is revealed in those posts as leeu14.
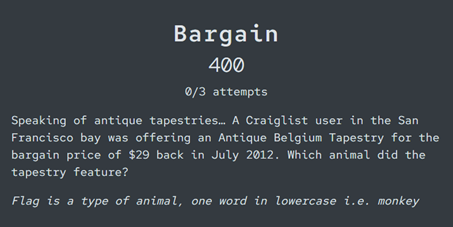
Bargain
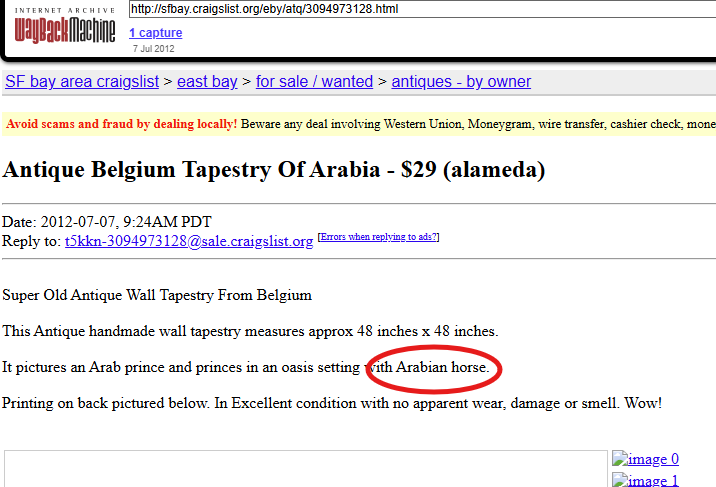
This challenge gives a few key clues: the ad was for an ‘Antique Belgium Tapestry’, listed for $29, and posted in the San Francisco Bay Area on Craigslist (another online marketplace).
To begin, we can identify the current version of the Craigslist antiques category for the SF Bay area: https://sfbay.craigslist.org/search/ata#search=2~gallery~0. While the listing itself is no longer live, this URL structure might be useful for searching in the Wayback Machine.
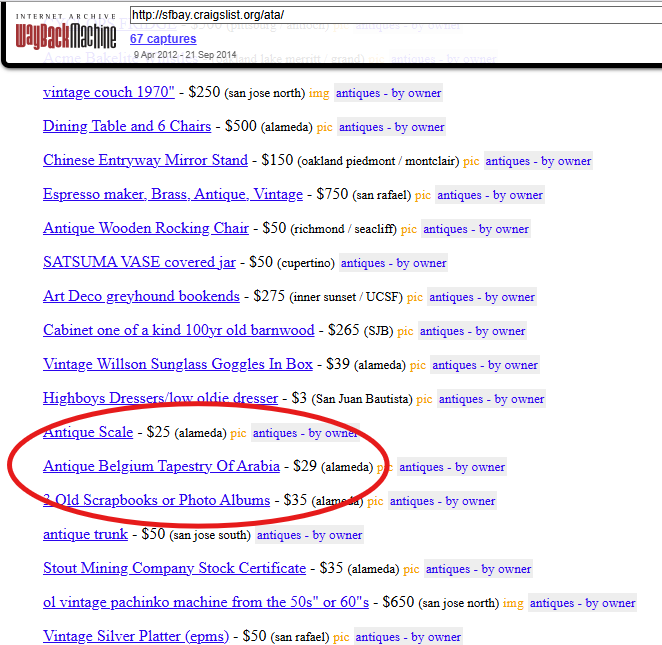
Searching the snapshots from July 2012, we can find three captures from that month. The relevant post appears in the July 7 capture (so hopefully you started with the captures at the beginning of the month, rather than the end!).
The relevant post reveals that the tapestry includes a horse, so we have our flag.
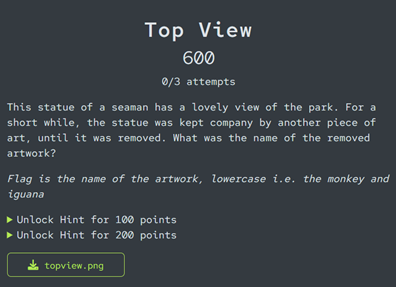
Top View
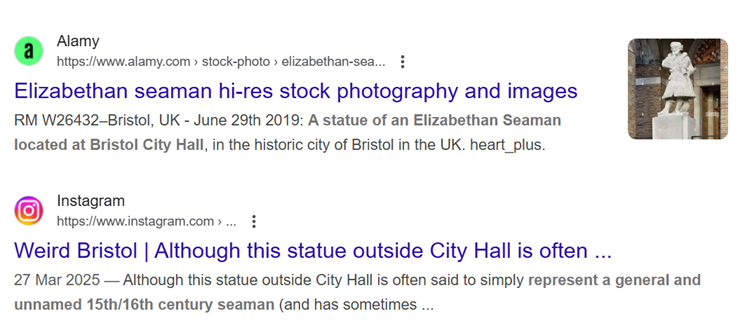
In this challenge, we are presented with a rear-facing image of a statue looking out over a grassy square, but without a clear view of the subject’s face or any identifying signs, the task requires a bit of creative geolocation. A standard Google reverse image search isn’t much help here, as it mostly suggests unrelated statues with a similar style. Google's AI overview might misidentify the statue as another maritime figure in Bristol – this is a false lead (although Bristol is indeed the correct city).
So, what other clues does the image offer? Well, we can see the following features:
A green or park of some sort.
Pedestrians and park-goers wearing clothes suitable for mild weather.
Three flagpoles, each featuring a different flag – we can see the colours, but not the patterns on each.
Large, mature trees in the background with heavy foliage.
Stone and brick surrounding the statue itself – it looks old, but not ancient.
A Google watermark with the year ‘2024’, indicating that this image is from Streetview.
Some sort of pond or water feature below the statue – it looks quite murky, so perhaps it isn’t cleaned very often!
A partial building in the top right corner with what appears to be a Gothic tower/pinnacle and finial (did we mention that knowing your architecture is a great way to improve your geolocation skills?)
Some lampposts and obscured buildings in the background.
The statue itself has a fancy, fur-lined robe, and there is a strange dolphin-like creature at his feet (why it’s emerging from beneath his robes is anyone’s guess!).
All of this information can help us verify that we do, indeed, have the correct statue. Now it’s just a matter of figuring out where it is…
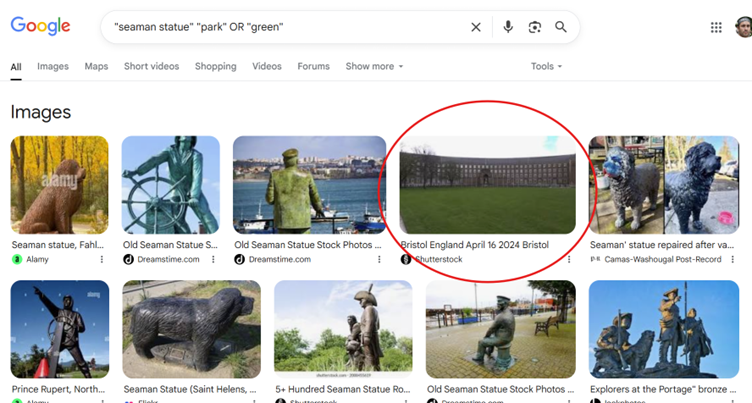
If we start building out a targeted search using descriptive terms like statue, seaman, and overlooking park, we can start to narrow down our options, or at least begin to rule out others.
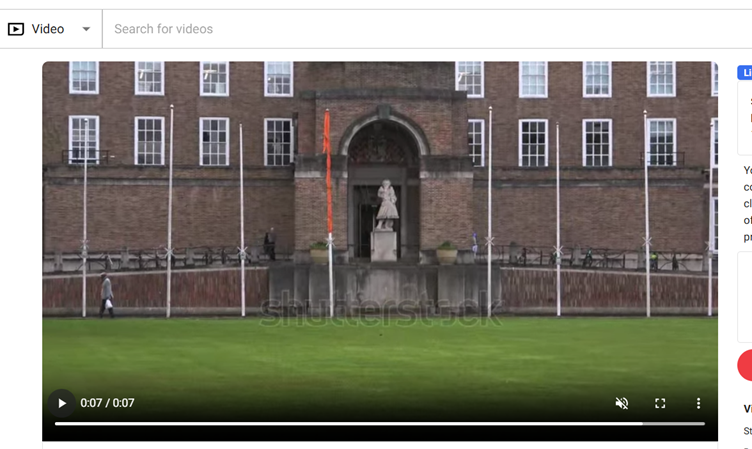
One of these results is a little too far away to make out properly, but if we click through to the Shutterstock video, we get a slightly better view. Anything look familiar?
For verification purposes, we can tick a few key features off straight away – the flagpoles, the building materials, and the green in front. So, let’s see if we find out the location name. A little more searching with the addition of ‘Bristol’ as a keyword should be enough to identify our statue.
he location is revealed to be the statue of an unnamed Elizabethan seaman, located at City Hall, College Green, Bristol.
From here, we need to figure out which artwork was removed from the area. Keyword searches might not yield as much as we hoped – the city of Bristol has also removed other controversial pieces, including a portrait of slave trader Edward Colston from within City Hall itself. We need to narrow things down a little more. There are certainly hints about the artist in question from search results, and I’m sure you’ve come across their name before.
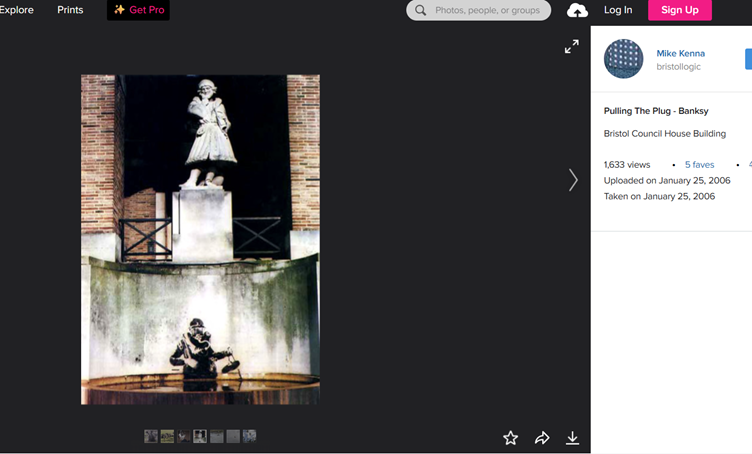
Banksy is probably the most well-known street artist in the world at this point. But which artwork kept the Elizabethan Seaman statue company at Bristol City Hall? We can start crafting searches to target information about Banksy artworks for that location – which, according to local websites, used to be known as the Council House. It might take some trawling, but combining search terms will help us to identify a Banksy work called ‘Pulling the Plug’ which featured directly below the statue in our image.
If you managed to get this challenge without resorting to hints, congratulations – it was a really tough one! Now onto our final challenge…
Banksy
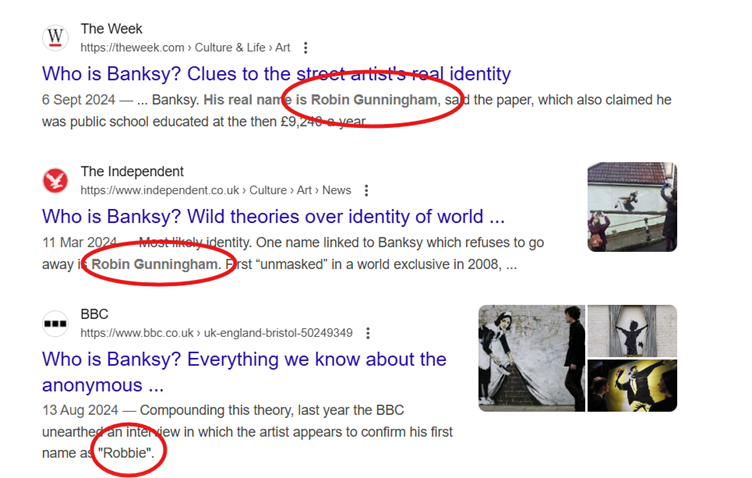
Our final challenge (at least if you managed to get the answer to Top View!) is a slightly cheeky one. Pulling the Plug was, of course, a work by Banksy, one of the most well-known ‘anonymous’ artists in the world. But how much do we really know about Banksy? Perhaps we can’t be one hundred percent sure, but there have been a number of exposes and articles published naming the most likely individual associated with Banksy’s works. A quick Google search will reveal the name Robert Gunningham from a number of articles:
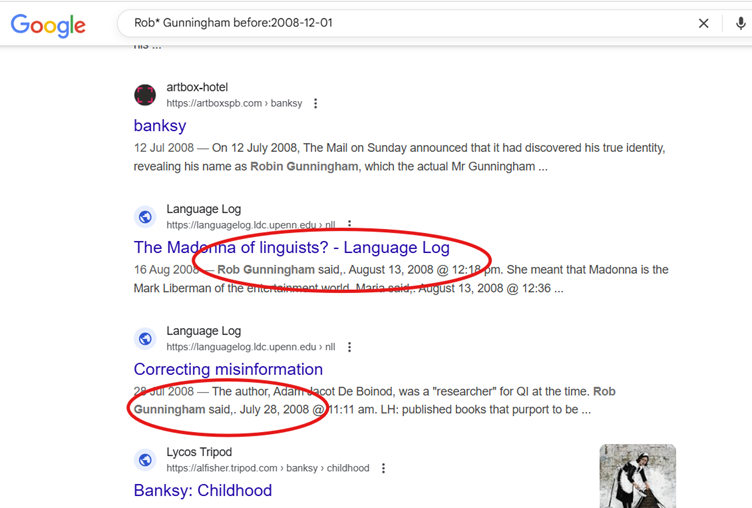
Let’s work on the theory that the name ‘Robert Gunningham’ is the correct one. Now we need to build out some searches to target content posted by him in 2008. We don’t know his username on the blog in question, but we can infer that it must be linked to his name somehow. This step might take a little longer (AI might be a useful assistant for generating variations of Gunningham’s name), but if we come up with a search string like the one below, we should be in luck.
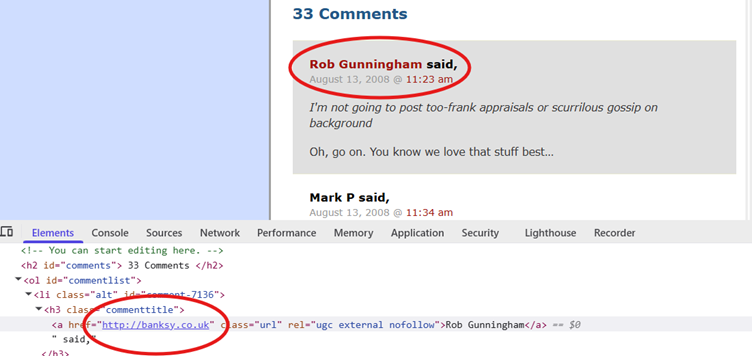
The top few results are news articles, but then we can see references to comments made by a user ‘Rob Gunningham’ in 2008.
Sure enough, Rob Gunningham’s profile links to none other than the official Banksy website. This was another tricky challenge, so well done if you managed to capture the flag!
How did you fare? There were some tricky ones in there! Our final scoreboard shows our top ten players, and jf2k was the unparalleled victor scoring all 5100 available points!
Congratulations on some excellent OSINTing! And thank you to all who took part – we hope you had fun and learnt some new tricks and techniques. Keep an eye out for our special upcoming Capture-the-Flag for the Australian OSINT Symposium September 18-19.