top of page
A New Era of Investigative Intelligence

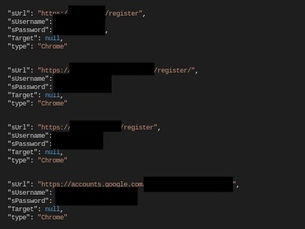
Stealer Log Blog
Info stealer malware can pull saved passwords, cookies, browser data and crypto details from an infected device, then bundle it into “stealer logs” sold or leaked online. This post explains what logs contain, how they differ from breached data, where they appear, and how OSINT and security teams can use lawful aggregators to track exposure safely.
5 days ago8 min read


Inside Discord: An OSINT Guide to Servers, Search and OPSEC
Discord has evolved far beyond gaming, becoming a rich source of information for investigators. This blog breaks down how the platform works, the OPSEC risks to watch for, and practical techniques for discovering, searching and monitoring Discord servers for OSINT.
Dec 10, 20256 min read


A Career Change into OSINT?
We’re often asked how people find their way into Open-Source Intelligence (OSINT), how they stay connected to the community, and keep growing in a field that doesn’t follow a straight line. In this blog, one of our longest-serving employees at OSINT Combine, Emerald, shares her path into OSINT — a reminder that there is no single way into this field, and there’s certainly no linear path once you’re in it. She reflects on navigating change, finding her footing, and discovering
Nov 22, 20255 min read


Australian OSINT Symposium Capture-the-Flag Walkthrough Part III
If you’ve been following along with our previous walkthrough blogs for the Australian OSINT Symposium Capture-the-Flag ( Part I and Part II ), you’ll know we have one final challenge left. This one was a tricky geolocation challenge, although it might have been a little more straightforward for those who were paying attention to some clues in the rest of the challenges. Transit Point This is a classic geolocation challenge – we have an image, without any metadata, and we nee
Oct 31, 20254 min read


Australian OSINT Symposium Capture-the-Flag Walkthrough Part II
It’s time for the Part II of our walkthrough for the Australian OSINT Symposium Capture-the-Flag. In this blog, we’ll talk through the tradecraft and techniques that players could use for each challenge – but, as always, there may be other paths to finding solutions. Pay Up The attachment for this challenge contains a series of text messages referencing a Bitcoin transaction. We have some key pieces of information to help locate the Bitcoin wallet address – firstly, the trans
Oct 27, 20258 min read


Australian OSINT Symposium Capture-the-Flag Walkthrough Part I
We were thrilled to host a phenomenal line-up of speakers and participants at the Australian OSINT Symposium in Sydney on 18 and 19...
Oct 13, 20258 min read


Why AI Agreeableness Poses Risks to OSINT Work
Sycophancy in AI has significant implications for reliability in OSINT.
Aug 26, 20256 min read


The Art of Deception: OSINT Capture-the-Flag Walkthrough Part II
This is the second part of our walkthrough for our July Capture-the-Flag The Art of Deception , in which more than 200 participants...
Aug 12, 20259 min read


The Art of Deception: OSINT Capture-the-Flag Walkthrough Part I
Part I: A walk-through for our July Capture-the-Flag challenge, The Art of Deception!
Aug 6, 20257 min read


Don’t Trust Your Gut (Until You’ve Tested It): Assumptions in Image Analysis and Geolocation
Explore the importance of testing assumptions in image analysis and geolocation.
Jul 16, 20256 min read


The Real Work of Building Enduring OSINT Capability
We’re not short on data—we’re short on time, context, and confidence. That’s where open-source intelligence (OSINT) comes in. Done well,...
Jun 25, 20254 min read


OSINT for Event Monitoring - Before, During, and After
OSINT is essential for monitoring major events, helping teams track risks in real time. This blog explores its role and shares free tools to support every stage of event monitoring.
May 14, 20256 min read

A Walk on the Wild Side: OSINT Capture-the-Flag Walkthrough Part II
In Part II, we tackle the next OSINT CTF challenges, looking at the methods to reveal the flags.
May 6, 202510 min read


A Walk on the Wild Side: OSINT Capture-the-Flag Walkthrough Part I
Capture-the-Flag Walkthrough Part I for OSINT Combine's "A Walk on the Wild Side"
Apr 30, 20258 min read


Using OSINT to Analyse China’s Two Sessions
Discover how OSINT techniques can help understand China's Two Sessions, revealing Beijing's priorities and plans through the collection and analysis of publicly available information.
Apr 14, 20258 min read


Insider Threat Mitigation with OSINT
Insider threats remain one of the most challenging security risks for organisations to manage, and the costs are high - recent statistics...
Apr 2, 20258 min read


OSINT’s Role When Geopolitics Cuts Deep
What happens under the sea affects us all. When Baltic cables were cut, OSINT tracked suspicious ships and exposed threats.
Mar 20, 20255 min read


Investigating Email Addresses with OSINT
Discover how to conduct an effective OSINT Email Investigation. Explore tools and techniques to uncover valuable information.
Mar 4, 20259 min read


OSINT in 2025: The Changing Landscape of Social Media and Technology
Explore 2025's major shifts in Gen. AI and social media, including DeepSeek's emergence, TikTok's US ban, and key implications for OSINT.
Feb 13, 20258 min read


Level up your OSINT with Fusion Skills
Discover the 5 essential fusion skills OSINT practitioners need to effectively collaborate with AI tools.
Feb 6, 20252 min read

Insights in OSINT
Explore in-depth articles, expert advice, and real-world applications to elevate your Open-Source Intelligence.
bottom of page
