The Art of Deception: OSINT Capture-the-Flag Walkthrough Part I
- Jemma Ward
- Aug 6, 2025
- 7 min read
Updated: Aug 12, 2025
In this two-part blog, we’ll provide a walk-through for our July Capture-the-Flag challenge, The Art of Deception! Over the past month, participants dove into a world of forgeries, fakes, and clever sleuthing, solving challenges inspired by art heists and online deception. Whether you cracked every flag or just want to see how it all came together, this blog will walk you through each challenge, explain the solutions, and highlight some of the trickier twists we threw in along the way.
Can I Speak to the Manager?
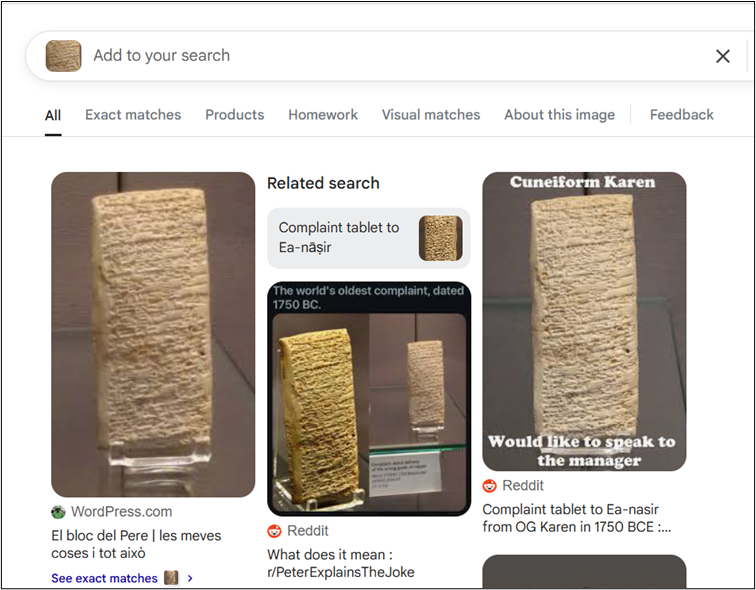
Some of you (any Tumblr users from circa 2010s?) might already have a pretty good idea of the answer to this one, but for others, you’re about to discover one of the oldest known customer complaints. A reverse image search of the attached file will reveal that the image in question is a tablet featuring a complaint about the quality of copper sold by Mesopotamian copper merchant Ea-nāṣir, circa 1750BCE.
Ea-nāṣir’s sub-standard copper, and customer Nanni’s complaint, has since become something of a meme on sites like Reddit and Tumblr. Just goes to show the lasting power of a bad review – you deliver bad copper one time, and people are still talking about it 3000 years later…
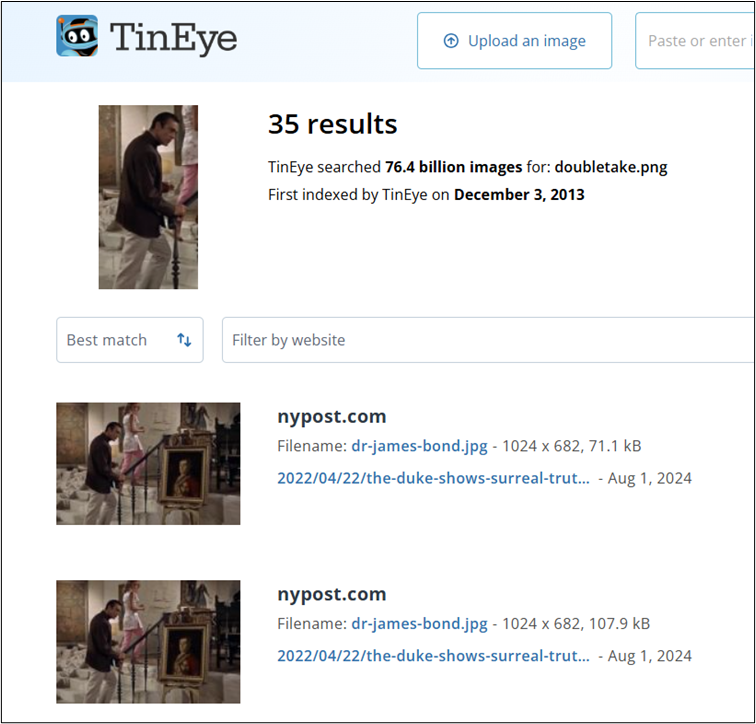
Double Take
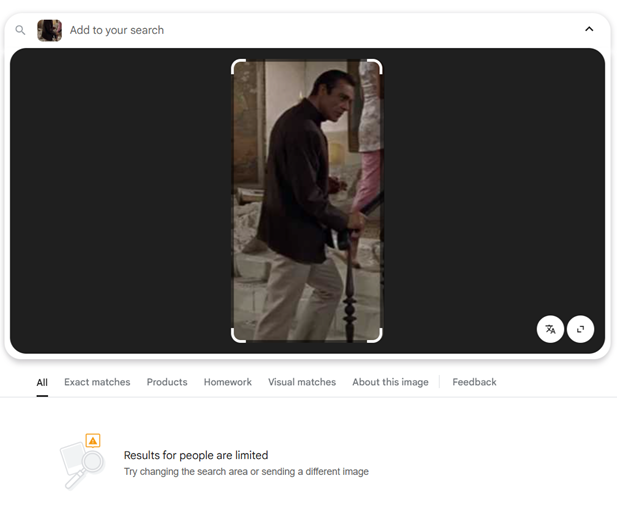
Another image searching challenge – but this time, Google may prove less than helpful when it comes to identifying the image:
This is where we need to branch out into other image searching tools. There are a few to choose from (and, of course, AI may be able to assist when it comes to identifying where this image is from. Here are our results when we search for our image using TinEye, a well-known image search engine.
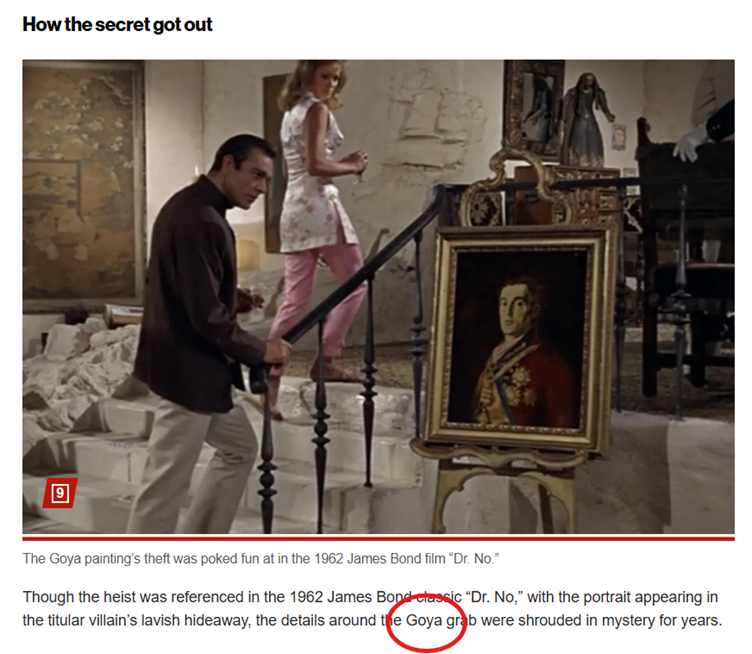
TinEye, as we can see, does indeed retrieve results that show us the full picture, including the painting. The filenames also give us a hint about the film still we’re looking at! It is, of course, from a James Bond movie – from ‘Dr. No’, specifically. The link containing the image provides a wealth of information about the stolen art piece, a portrait of the Duke of Wellington by Francisco Goya. It was stolen from the National Gallery in London in 1961 but later returned.
Off to the Shop
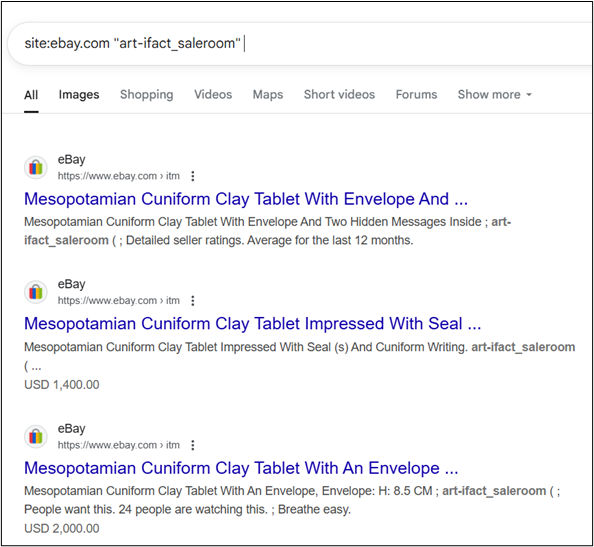
In Off to the Shop, we are asked to determine the city in which an eBay seller, art-ifact_saleroom, is apparently located. This challenge is focused on navigating online marketplaces. To solve it, we need to find the seller’s profile page.
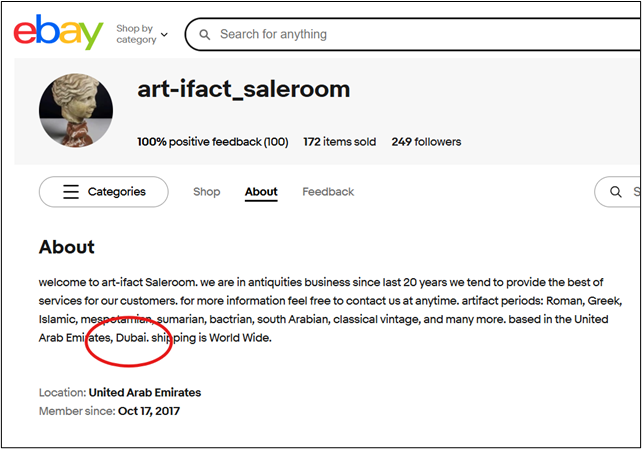
Our next step is to navigate to the user profile page, which can be found at ebay.com/usr/art-ifact_saleroom. The ‘About’ section of the profile tells us that the seller is based in Dubai, in the United Arab Emirates. Another flag captured!
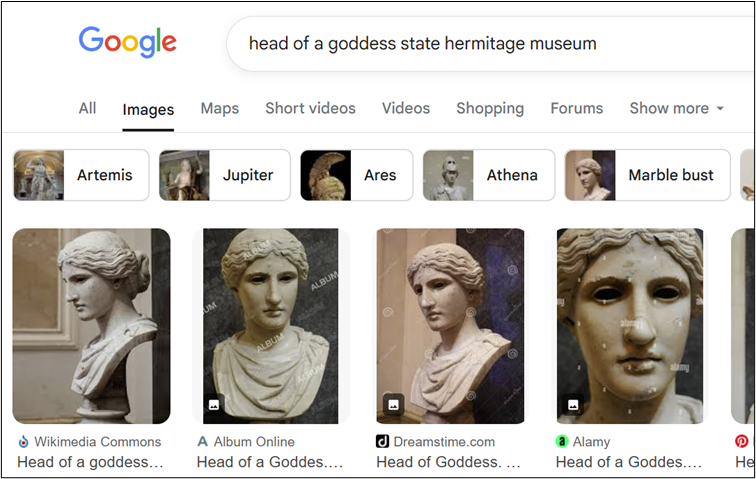
Goddess
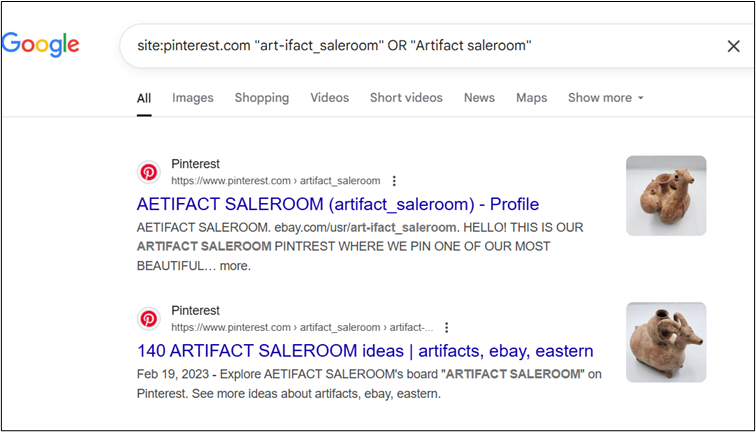
This is a follow-on challenge from Off to the Shop – we need to find the user’s Pinterest account and identify the location of the profile picture. So, let’s search for Pinterest accounts containing the eBay user’s account name, or variations thereof. Something like the below will get us to the right result.
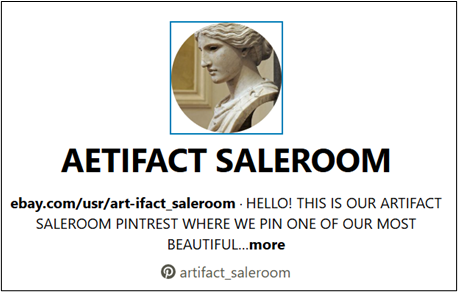
The profile picture appears to be of a statue. Reverse image searching is a sensible next step, although in this case, we might find that Google (and Bing as well) suggest similar pictures, but not exactly the same one.
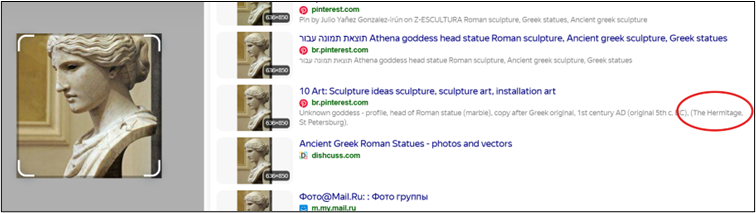
But there’s another widely used search engine that we might try – although Yandex image search might not be quite as effective for some Western centric content, it’s really useful for retrieving images from social media and Russian sites. Sure enough, we have plenty of results from a Yandex image search.
Lots of these results point to the likely location of the statue – the State Hermitage Museum in Saint Petersburg. With a little searching, we can verify that this is indeed the correct location.
Snowy Day
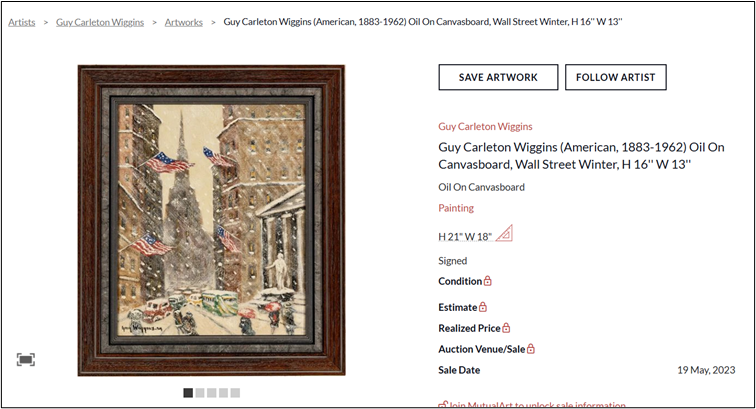
This is a surprisingly tricky one – initial searching, along with AI, will likely report that this is a painting by Wiggins, but, as always in the OSINT world, we need to spend a little more time verifying initial details and checking our assumptions.
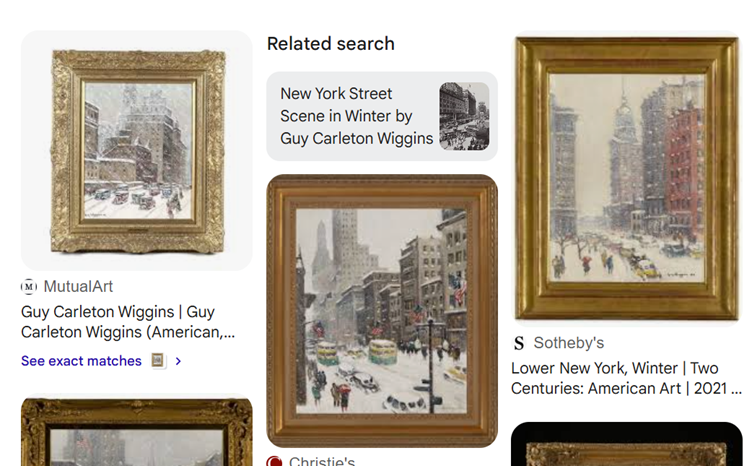
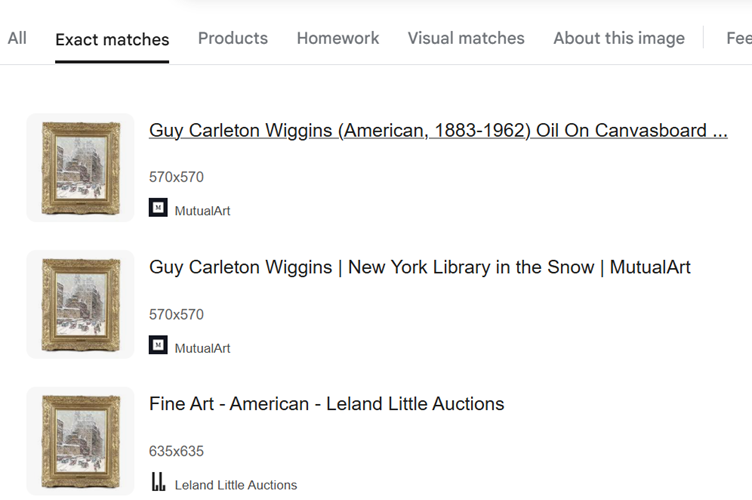
Even when we look at the ‘Exact Matches’ within Google image search, we’re presented with the same information – this is a painting by Guy Carleton Wiggins, of a snowy day in New York.
But when we click through to the result, we actually see a different painting…
Turns out that Wiggins actually painted a number of New York streetscapes that look surprisingly similar! The one you see above, with the American flags, is, apparently, genuine! But where has our image gone? If we scroll down, we can see it… But this time it’s not listed as a Wiggins.
Now, if we have a closer look at this painting, we can see a signature apparently belonging to Wiggins – but keep scrolling through, and we actually find a letter from Wiggins’ son pronouncing it to be a fake. Not so genuine after all!
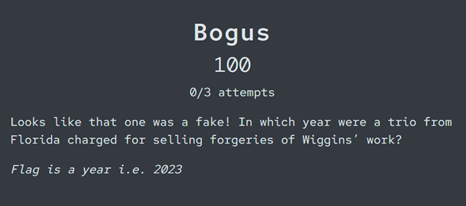
Bogus
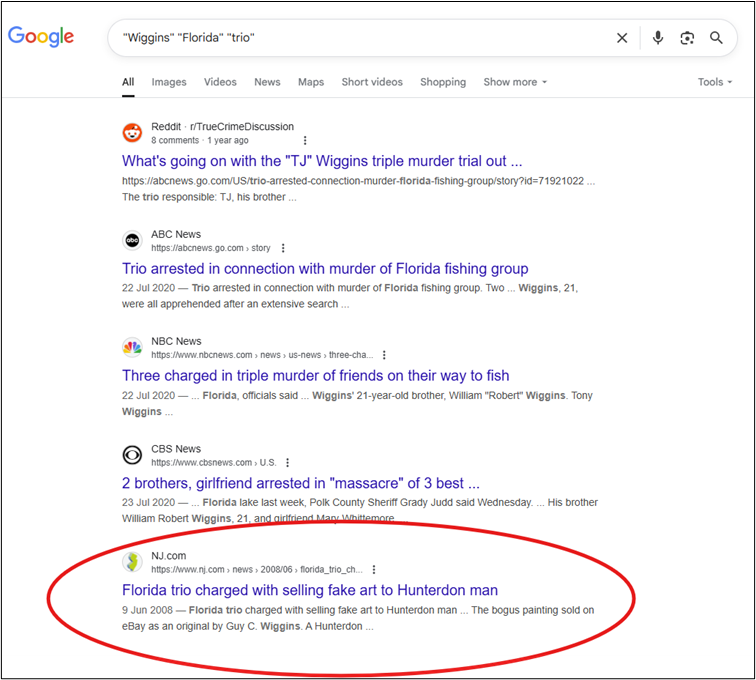
Another follow-on challenge, this time from ‘Snowy Day’. This one should be a straightforward matter of crafting a search string to identify the correct year. We have some keywords that we can use: Wiggins, Florida, trio.
A very basic search gets us the answer, although it’s still not the top result:
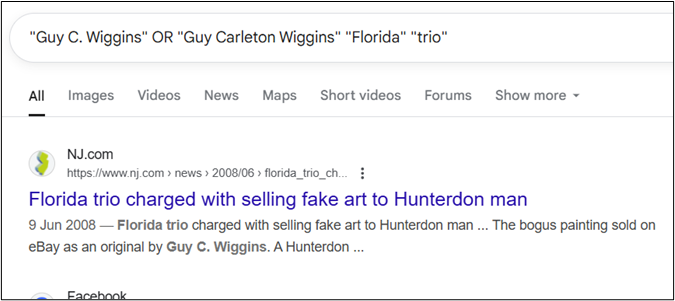
To refine your Google search results, think about including unique parameters – for example, instead of just using ‘Wiggins’ as a term, we could include variations of the artist’s full name. Sure enough, that gets us there just that little bit faster.
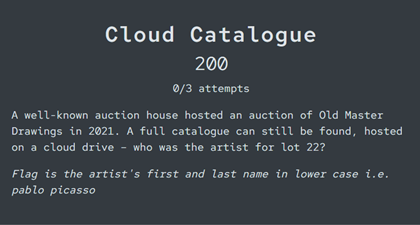
Cloud Catalogue
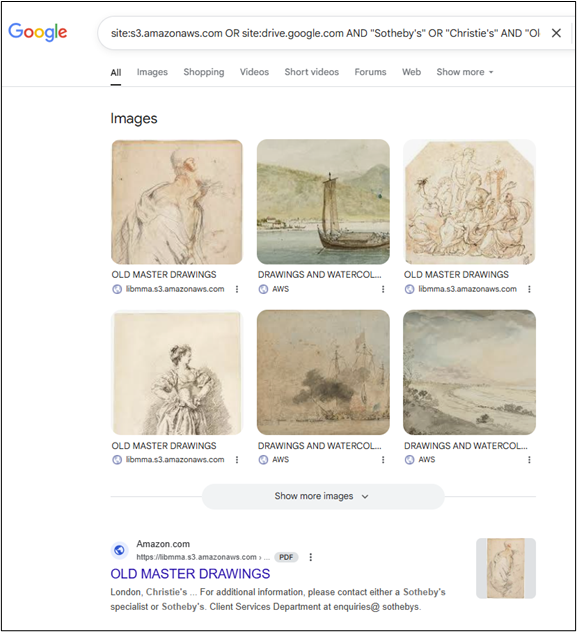
There are several clues in the wording of this challenge to help us out. Firstly, we know that this catalogue is stored on a cloud drive. There are a few common ones that we might choose to target. Did you know that you can create Google dorks to target cloud drives using the site: operator? You’ll just need the domain of relevant cloud drive providers.
We also know that this catalogue was for an auction hosted by a ‘well-known auction house’. You probably have a couple of ideas off the top of your head (Christie’s? Sotheby’s?), but a little bit of Google research should confirm the top auction houses for art and antiques. No surprises there.
By combining terms like ‘Sotheby’s’, ‘Old Master Drawings’, and ‘2021’, while targeting cloud drive domains, we should be able to identify the catalogue in question:
Sure enough, lot 22 (on page 31) shows the artist name as Abraham Bloemaert.
Cat's Meow
Most social media platforms will assign unique identifiers for accounts. Sometimes these are visible, sometimes not. For OSINT investigations, particularly where long-term monitoring of accounts is required, it’s important to collect these identifiers where possible – it means that if the account vanity name or handle changes, you’ll still be able to find the account.
Finding X account identifiers isn’t too difficult, but unlike Facebook, it won’t appear in the page source, so you’ll need to dust off your Developer tools. First, you need to navigate to the account of interest, then follow these steps:
Open Developer tools (right click > ‘Inspect’, or Ctrl + Shift + I in most browsers)
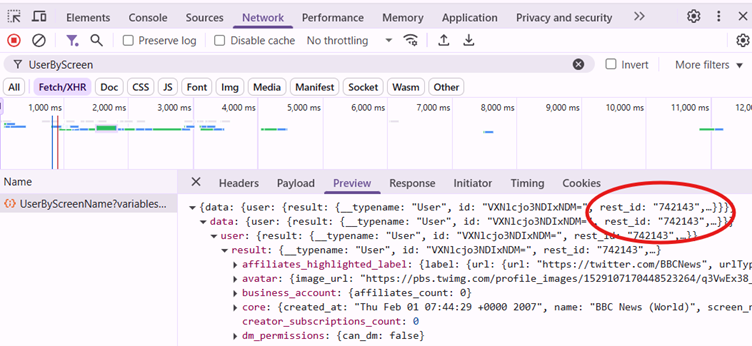
In the Network tab, select the Fetch/XHR filter and enter the text below into the keyword filter: UserByScreen
Refresh the page. One result should load.
Navigate to ‘Preview’ tab and expand user data fields. You are looking for the ‘rest_id’ – the number following is the user’s unique profile identification number.
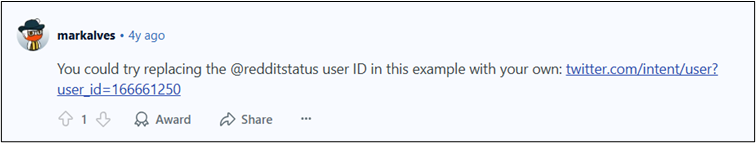
A little bit fiddly, but fairly straightforward. But what about reversing the process? If we have a unique identifier, how can we link it to an account? Unfortunately, sites like tweeterid.com no longer seem to retrieve a username based on an account ID. Instead, this is where we can use one of Twitter’s old rest_id look-up URLs. Most of us probably don’t know the URL off the top of our heads, so you might have had to search for it in OSINT tradecraft spaces and guides. In this case, there’s a Reddit thread that looks promising…
One of the responses includes a URL to retrieve a username from a user_id:
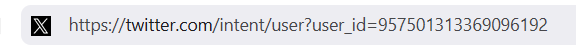
The format for the URL is: https://twitter.com/intent/user?user_id=XXX (but replace XXX with user’s rest ID). To try it out, we take the URL, and add our profile of interest ID:
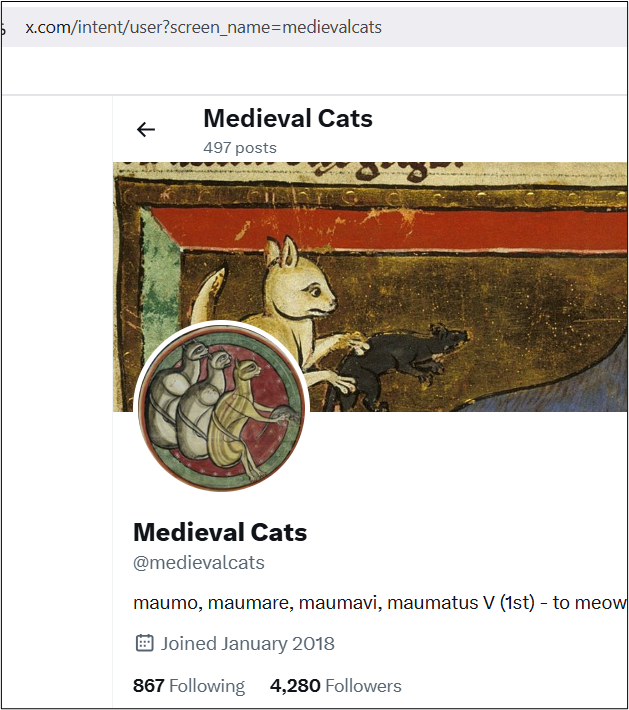
This should retrieve the user’s account page, in this case:
From there, we can copy and paste the handle (@medievalcats) and we have our flag!
Fabulous Fabiola
Our first step for this challenge is to identify the original Reddit post. We have a few clues in the wording of the challenge – we know that the subject of the painting is Saint Fabiola, and there’s a reference to a ‘family heirloom’. The post is likely to be on a subreddit related to art or antiques.
Using keywords like Fabiola and family heirloom in a Google or Reddit search lead fairly quickly to a relevant post on Reddit’s r/WhatIsThisPainting subreddit:
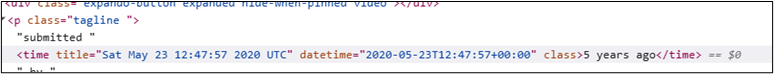
Reddit’s visible timestamps don’t always show the precise posting date. To find the exact date, we need to view the page source (right-click > View Page Source) and search for a timestamp in the HTML. This should reveal the correct date, in this case, 23 May 2020.
The correct flag is 20200523.
Paris
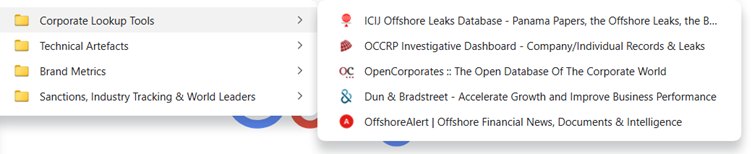
Hmm, this sounds like we need some corporate look-up tools. You’ll find a selection of corporate and business record tools in the ‘Corporate Profiling’ folder of our OSINT Bookmark Stack:
There are also a range of country-specific corporate look-up tools, and the amount of data you can retrieve depends on the location, but sites like OpenCorporates and Dun & Bradstreet are a good starting point, as they cover corporate registrations in a lot of jurisdictions.
Let’s try out OpenCorporate for this challenge. We have an address – 8 Rue Lallier – but not the company name. Unfortunately OpenCorporates doesn’t let us search for the registered address without an account, so we’re going to have to cross-check.
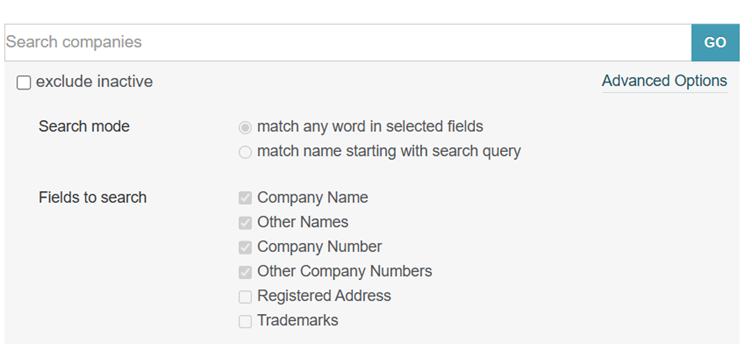
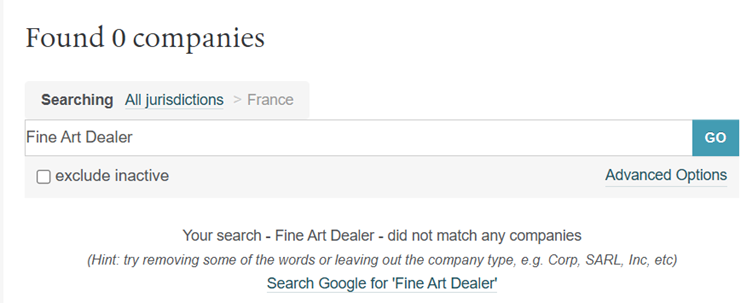
We know, though, that we can restrict our jurisdiction to France, which will narrow down our results a lot more. Let’s try the search term we’ve been given in the challenge ‘Fine Art Dealer’.
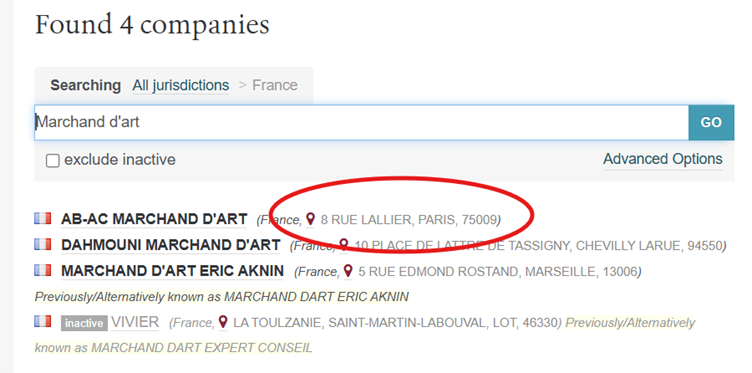
No luck there – but that makes sense, as we’re looking for a French company, so the company name is unlikely to be in English. Let’s translate ‘Fine Art Dealer’ into French and conduct the search again.
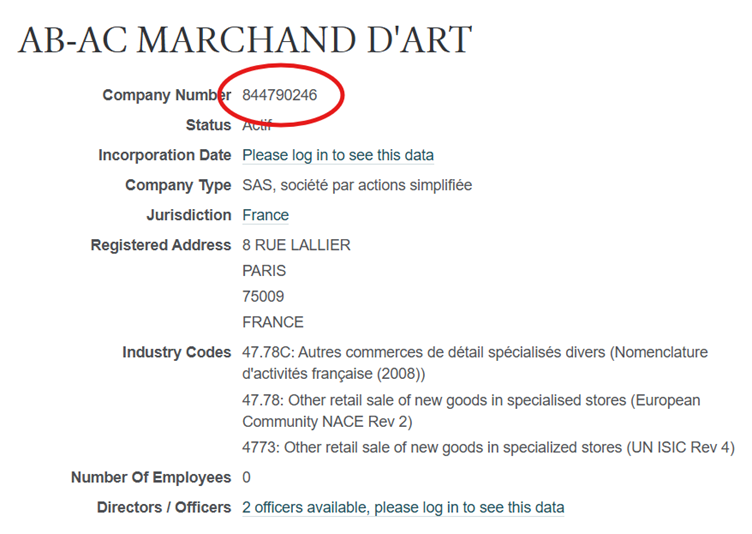
We’ve found our company listed at 8 Rue Lallier, Paris. If we click through, we can find the company number listed – 844790246.
That's our first ten challenges explained - stay tuned for Part II of our walk-through. Want to learn more about how open-source intelligence can be leveraged for art crime investigations?
In the Open Secret episode Protecting Priceless Things: OSINT and Art Crime, hosts Kylie Pert and Jane van Tienen take a deep dive into the world of stolen art and antiquities with Tim Carpenter, Managing Director and CEO, Argus Cultural Property Consultants. Listen here.