Australian OSINT Symposium Capture-the-Flag Walkthrough Part II
- Jemma Ward
- Oct 27
- 8 min read
It’s time for the Part II of our walkthrough for the Australian OSINT Symposium Capture-the-Flag. In this blog, we’ll talk through the tradecraft and techniques that players could use for each challenge – but, as always, there may be other paths to finding solutions.
Pay Up

The attachment for this challenge contains a series of text messages referencing a Bitcoin transaction.

We have some key pieces of information to help locate the Bitcoin wallet address – firstly, the transaction took place on the ‘last day of the year’, which is 31 December 2024. Secondly, the amount transferred was equivalent to 66 594 USD. We can’t look up an individual’s bank account transfers – these are private, and for good reason! So why can we look up a cryptocurrency transaction? The answer, of course, is the blockchain.
Blockchain is a digital ledger technology that records transactions across a network of computers. Each block contains a list of verified transactions linked to the previous one, forming one continuous chain. While this data is secure and cannot be tampered with, it is also public, so anyone can view transaction histories for cryptocurrencies like Bitcoin. Tools such as Blockchair allow users to search and filter this blockchain data (for example, by wallet address, transfer amount or time) to trace and analyse specific transactions.
Blockchair allows advanced Bitcoin transaction searching, so we can use the information in the challenge to filter transactions. Let’s look for transactions on 31 December 2024 that have a transfer amount of 66 594 (we can either use the exact amount filter or the ‘between’ filter).

The matching transaction has the TXID e2147c55d9ac4dc2635936f9536cb2657b4c93d8f98f4689ff225372da7353be.
Open the transaction result to see the inputs/outputs – the output shows that the receiving address is: 3HgNSooXGzfTzpp8TRzViMVoq1XLHLEwTj.

Rainy Day

In this challenge, we have another text conversation:

The phrasing of the challenge, and the hints in the text messages, suggest that you will need to find some official rainfall records. A quick google of Australian rainfall records should lead you to the Bureau of Meteorology website.

While many OSINT practitioners are unlikely to need this specific set of records, understanding how to search and navigate weather records and archives is a useful skill across a range of topics and issues – it can help us with establishing times and locations for videos or images, as well as provide context for area and event monitoring.
BOM’s Climate Data Online (CDO) allows searching of weather station records by year, so we can use the CDO text search to identify a likely weather station – Sydney Botanic Gardens. From here, we can retrieve the records and navigate to 1984.

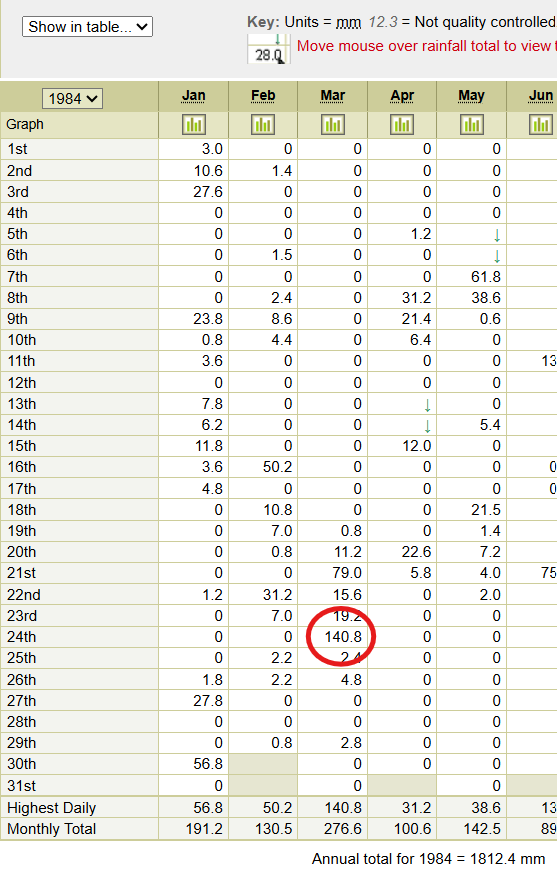
The records table shows that the highest rainfall in March 1984 was 140.8.
Discord

For this challenge, we need to locate a Discord server, possibly with the name ‘Weather Club’. While Google may assist with locating Discord servers of interest, there are also Discord-specific search engines that will pull back top server results. These include:
Using Disboard (one of the top results for Discord server search engines), search for key terms such as ‘weather’ or ‘weather club’.

We can see that ‘Weather Club’ has received one five-star review, and clicking through to view the review shows that it was left by someone with the username ‘f1vettel_fan’.
Discord II

This is a follow on challenge from our previous Discord flag. Unfortunately, Disboard search doesn’t show the server creation date – there is, of course, the option to join the Weather Club server and see the creation date, but this would require a Discord account. In our walk-through for the challenge above, we mentioned some other Discord search engines, including Discadia, which does show the server creation date.
As before, we use the tool to search for our server of interest (‘Weather Club’), and Discadia’s server profile shows the creation date of 20230928.

Paradise

In the Corporate Profiling section of our OSINT Bookmark Stack, you’ll find a link to the ICIJ Offshore Leaks database. This is searchable resource containing records from financial investigations of the Paradise Papers, Panama Papers, Pandora Papers, and more. When undertaking open-source research on corporate entities, financial investigations can reveal previously unknown or unpublicised connections between people and companies. The site’s search tools allow you to look up names, jurisdictions, or company types and trace links between entities across leaked datasets.
If we search for ‘Temple Street’ in the database, the first result is for an entity called ‘Temple Street Investments’ – it seems a likely candidate based on our clues!

Viewing this result shows a connected entity called ‘Elco Corporate Services Limited’.

Bulgaria

In this challenge, we’re given a few handy clues, including the street name, city, and the fact that the company in question is Bulgarian with a name similar to ‘Elco’. Using targeted search strings, we can locate export or business databases, one of which lists a company called ‘Elko’ with an address in Gabrovo Street, Varna.

If we click through and examine one of the bills of lading, we find the company’s contact details, including the Yahoo email address - orion_vbg@yahoo.com.

Secondary Address

In this challenge, we learn that there is another email address – this time a Gmail account – associated with Elko Ltd. There are a couple of approaches that work here – we can use Google to construct targeted search strings, which retrieves the correct Gmail address from a preview of Elko’s Facebook account.\

Sometimes it’s easier to go straight to a company’s online assets (websites and social media pages) than trying to crack the correct search string, though. Searching for Elko Ltd along with a location-based keyword will retrieve the company’s Facebook page, and scrolling through recent posts will reveal an image containing all contact details, including the Gmail address.

Confidential

The key to this challenge is metadata – we have a PDF file (which contains some mysterious references to Temple Street Import’s dubious line of business), but the flag itself doesn’t seem to be present in the visible text. The key to this challenge, therefore, is likely to exist somewhere in the file metadata.
Metadata is the hidden information stored within digital files that describes a file’s properties and history. For documents like PDFs, this can include details like the creator’s name, the software used, the creation and modification dates, and sometimes information about the organisation or device that produced it. Analysing metadata can help investigators understand its origins, and whether it has been modified. In open-source investigations, metadata often provides valuable context that isn’t visible in the content itself.
To check the PDF’s metadata, we can open the file in a PDF viewer or browser, and then select the option to ‘View Document Properties’. This shows us the name of the creator, when the file was created, as well as our flag – the Latin phrase mors janua vitae.

Missing

For this challenge, we need to find a newspaper report from 1st January 1926. The disappearance of the SS Cotopaxi was, of course, a significant enough news story that many newspapers reported on it, and we found other reports on other dates within a similar timeframe, but not for this specific date. By way of caveat, we do not necessarily have access to some region-specific newspaper archives, so there potentially may have been another correct answer that we couldn’t see when we created this challenge!
While most countries, and often towns and cities, maintain digital archives of newspapers, they often require subscriptions or special access (resources like https://www.britishnewspaperarchive.co.uk/ are well worth the subscription fee if old newspaper articles are of interest, but there’s limited access for unregistered users). As OSINT practitioners, we usually want to exhaust freely available archives before we sign up or subscribe to anything.
That’s where the Internet Archive comes in. The Internet Archive is a vast online repository that preserves historical materials such as newspapers, radio and TV broadcasts, books, and open-source publications. Most OSINT practitioners are familiar with the Internet Archive’s Wayback Machine but may be less used to searching the text and multimedia section of the archives. It’s well worth coming to grips with, though, because the Internet Archive provides free access to content that may no longer exist elsewhere online. It can assist in tracking historical events, tracing media narratives, or verifying the origins of information.
There is an advanced search feature, but it’s worth keeping in mind that digitised texts may not always have the exact spelling or phrasing that we are looking for, so it’s often more efficient to conduct a broad keyword-based search of text contents, and then narrow down the datetime parameters in the results pane.
When we search for ‘SS Cotopaxi’ in the text contents, and then narrow down results to 1926, we can see one result from the Victoria Daily Times, dated 1st January 1926.


Within that issue, there is a short article reporting on the disappearance of the ship.

Adrift

Looks like we’ve come across some fake news! Spoiler alert – the SS Cotopaxi was not found adrift by the Cuban Coast Guard in 2015. The wreck of the Cotopaxi lies about 35 nautical miles off the coast of Florida. But this mysterious VK user was sharing a different version of events…
We have some very specific information in the wording of this challenge, so it’s useful to draw out the key details:
The platform is VKontake, the Russian version of Facebook.
The user posted sometime in the first half of 2023.
The post presumably mentioned ‘Cotopaxi’, ‘Cuban Coast Guard’, and the apparent year of discovery, ‘2015’.
Russian search engine Yandex tends to index a lot of VK content, but, since the retrieved content is often in a different language, it can struggle with exact phrases. A more general keyword search, targeting VK.com, does yield some results, but often from the wrong timeframe.

Open Measures is a platform that gathers and visualises publicly available data from a range of niche and alternative media sites. While broad searching and data retrieval is limited, users can still perform keyword searches for content from platforms such as VK, Gab, Telegram and 4chan that may not be indexed by mainstream search engines. Open Measures is particularly useful tool for exploring disinformation narratives, trends and activity across issue-motivated groups and platforms.
We can conduct a basic search using keywords and date parameters and select our platform of interest (in this case, VK).
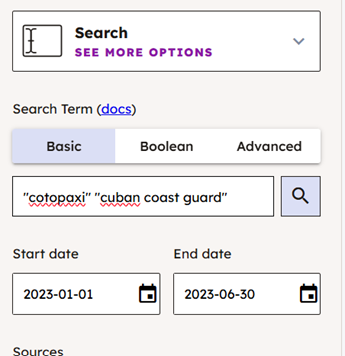
If we limit our search to the first half of 2023 (we can always refine it further if needed), and search for the keywords “Cotopaxi” and “Cuban coast guard” we retrieve a number of posts with tangential mentions of Cotopaxi, but one post in particular, by user ‘smoegodvora’, appears to be relevant.

A translation shows that we have the right account:

Devilry

There are a few methods for finding this flag, and we have some hints in the wording of the challenge that might assist us. There is a reference to a Python (.py) file, as well as code repositories, which tells us where we might begin our search.
Code repositories are platforms that host and share software source code, allowing developers to collaborate on projects. Examples include GitHub, GitLab, and Bitbucket, which contain huge amounts of open-source code from around the world. Because these repositories are publicly accessible, they can be searched for specific snippets, functions or keywords.
Unfortunately, a great code repository search tool, searchcode.com, is no longer online (it made grabbing the flag for this challenge very straightforward!), but we can also retrieve relevant results from Google searching, for example:

For this challenge, it was more effective to search for the phrase “SS Cotopaxi”, as searching for just “Cotopaxi” retrieves many results about an unrelated software package. The GitHub result you can see in the screengrab above contains excerpts from the correct .py file, although the page itself is in Chinese. We can either scroll through or use Ctrl+F to find the excerpt with the SS Cotopaxi reference, and then look for the subsequent set of coordinates:

A little further down, we can see the set of coordinates:

If we search these coordinates (44.590533, -104.715566) in Google, they will resolve to a location called ‘Devil’s Tower National Monument’. The flag is the first two words – ‘Devil’s Tower’.

NB: For this challenge, we realised that our CTF platform doesn’t accept certain kinds of apostrophes, so the flag was updated to ‘Devils Tower’ with no punctation.
How did you fare so far? There were some difficult challenges covered here, along with a variety of tools and techniques that you might not have come across before. We have one challenge remaining - Transit Point - which deserves its own blog, so keep an eye out for that, as well as our final scores for the 2025 Australian OSINT Symposium CTF.



